In an era where the digital landscape is constantly evolving, cybersecurity is a top concern for businesses and organizations of all sizes. One particular threat that has gained notoriety over the years is Distributed Denial of Service (DDoS) attacks. These malicious actions can cripple online operations, disrupt services, and cause significant financial losses. To fortify your network against DDoS attacks, it’s crucial to understand the interplay between DDoS attacks and Domain Name System (DNS) infrastructure.
Unmasking the DDoS Threat
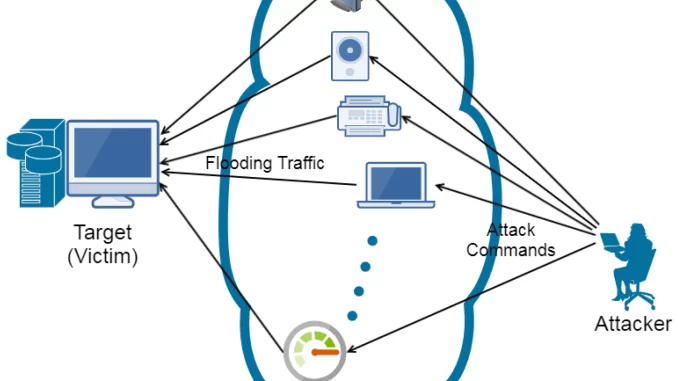
DDoS attacks involve overwhelming a target server or network with an excessive volume of traffic, rendering it inaccessible to legitimate users. Cybercriminals typically employ a multitude of compromised devices, creating a botnet, to amplify the attack’s impact. DDoS attacks come in different forms, including the more traditional volumetric attacks and the increasingly common application-layer attacks, designed to exploit vulnerabilities in specific services or applications.
The Role of DNS in DDoS Attacks
DNS is the critical system that translates human-readable domain names into IP addresses, allowing us to access websites by typing in their URLs. This process is integral to the functionality of the internet. Unfortunately, it also makes DNS infrastructure a prime target for DDoS attackers.
- Traffic Amplification: DNS servers can be manipulated to amplify traffic during an attack. Cybercriminals can use open DNS resolvers to send a small request that triggers a significantly larger response to the victim’s IP address. This technique magnifies the volume of data sent to the target, intensifying the DDoS attack.
- DNS Reflection Attacks: Attackers may exploit open DNS resolvers to redirect and reflect their attack traffic towards the victim’s servers. This can lead to a deluge of incoming traffic that the victim’s network is ill-equipped to handle.
- DNS Flood Attacks: Attackers can flood a DNS server with an overwhelming number of requests, causing it to become unresponsive. This, in turn, disrupts the target’s ability to resolve domain names and access online resources.
Defending Your Network Against DDoS Attacks
To safeguard your network against DDoS attacks, particularly those targeting DNS infrastructure, there are several critical measures you can implement:
- Web Filtering: Employ robust web filtering solutions that can detect and mitigate malicious traffic. Web filtering helps to identify and block unwanted or suspicious requests before they reach your network, minimizing the risk of DDoS attacks.
- Anycast DNS: Implement Anycast DNS to distribute DNS servers across multiple locations. This ensures redundancy and load balancing, making it more challenging for attackers to pinpoint a single target.
- Rate Limiting: Configure your DNS servers to impose rate limits on incoming requests, preventing them from becoming overwhelmed by excessive traffic.
- DDoS Mitigation Services: Consider utilizing DDoS mitigation services from trusted providers. These services employ advanced techniques to identify and filter out malicious traffic, allowing legitimate requests to pass through.
- Regular Patching and Updates: Keep your DNS software and infrastructure up to date to mitigate vulnerabilities that could be exploited by attackers.
- Monitoring and Incident Response: Continuously monitor your DNS infrastructure for signs of abnormal behavior. Have a well-defined incident response plan in place to mitigate DDoS attacks quickly.
In Conclusion
DDoS attacks targeting DNS infrastructure remain a significant threat in the cybersecurity landscape. Understanding the vulnerabilities and implementing proactive defenses, such as web filtering, is essential for protecting your network. By taking these measures, you can fortify your organization’s digital presence and reduce the risk of falling victim to disruptive DDoS attacks.

Leave a Reply